Fern Wifi Cracker is a Wireless security auditing and attack software program written using the Python Programming Language and the Python Qt GUI library, the program is able to crack and recover WEP/WPA/WPS keys and also run other network based attacks on wireless or ethernet based networks.
Today we reveal Fern Wifi Cracker free download, an open-source Pro wireless audit tool. It can crack as well as recover WEP, WPA, WPA2, WPA3, and WPS keys and also able to run other network-based attacks on the Ethernet or wireless-based networks. It is compatible with various Linux OS and can also be run on Windows 10 using virtualization. Reaver download below, this tool has been designed to be a robust and practical tool to hack WPS Pin WiFi Networks using WiFi Protected Setup (WPS) registrar PINs in order to recover WPA/WPA2 passphrases. It has been tested against a wide variety of access points and WPS implementations. The original Reaver implements an online brute force attack against, as described in here. Fern Wifi Cracker: wireless security audit tools Fern Wifi Cracker is a Wireless security auditing and attack software program written using the Python Programming Language and the Python Qt GUI library, the program is able to crack and recover WEP/WPA/WPS keys and also run other network based attacks on wireless or ethernet based networks.

The Software runs on any Linux machine with prerequisites installed, and it has been tested on Ubuntu KDE/Gnome, BackTrack Linux and BackBox Linux.
What is a Wifi Cracker
A Wifi Cracker is a tool or piece of software designed to help with the recovery of Wireless Access Point (WAP) keys from WPA2 or WPS secured networks.
There are various Wifi Cracker tools available such as:
– Infernal Twin – Automated Wireless Hacking Suite
– FruityWifi – Wireless Network Auditing Tool
– wifite – Mass Wifi WEP/WPA Key Cracking Tool
– Kismet – Wireless Network Hacking, Sniffing & Monitoring
Features of Fern Wifi Cracker
Fern currently supports:
- WEP Cracking with Fragmentation,Chop-Chop, Caffe-Latte, Hirte, ARP Request Replay or WPS attack
- WPA/WPA2 Cracking with Dictionary or WPS based attacks
- Automatic saving of key in database on successful crack
- Automatic Access Point Attack System
- Session Hijacking (Passive and Ethernet Modes)
- Access Point MAC Address Geo Location Tracking
- Internal MITM Engine
- Bruteforce Attacks (HTTP,HTTPS,TELNET,FTP)
- Update Support

Install Fern Wifi Cracker
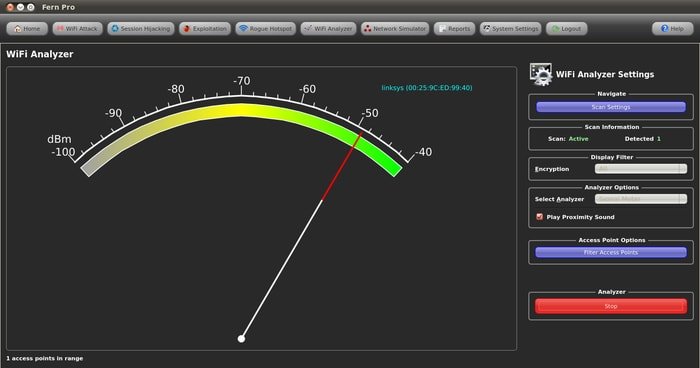
Fern Wifi Cracker Download
Prerequisites for Fern Wifi Cracker
Fern requires the following to run properly:
- Aircrack-NG
- Python-Scapy
- Python Qt4
- Python
- Subversion
- Xterm
- Reaver (for WPS Attacks)
- Macchanger
You can download Fern Wireless Cracker here:
Or read more here.